Another common misconception is that all reputable websites are safe. Compromising legitimate websites with infected code is one of the easiest ways to convince potential victims to download files or provide sensitive information.
- A rootkit is a software package designed to give attackers “root” access or admin access to a given system.
- Though you are unable to use the corrupted files, you can still repair and recover them with some free online tools like Registry Mechanic.
- Since the causes of disk errors vary from bad sectors, improper shutdowns, malware, corruption, physical damage, etc., the ways to check disk in Windows 10are from being easy to powerful.
Don’t show anyone else ;-),” you opened the attachment. This was how the Melissa virus spread and it played on the public’s naiveté about how viruses worked up to that point. Viruses of this type hide within the macro language commonly used in Microsoft Office files.
Part 3: How To Prevent Data Error Cyclic Redundancy Check External Hard Drive?
Scan your computer with your anti-virus application and remove any threats it detects. Viruses and Spyware can cause error messages on your PC and may be the source of your current issue.
Scholarpill.com has the most amazing customer service agents. I was having a hard time completing my 18 page Essay; as I have other things in Life to do as well. After hiring a professional writer from the website, my paper was delivered in half the time. Any minor revision requests I had were made very promptly, and all for 25% discount. This software will begin scanning the chosen hard drive or partition, and display the recovered files in the plate. Computer viruses & other types of malware are a constant & evolving threat to all computer & mobile device users. Confidential data, such as passwords, are a key target of cyber criminals.
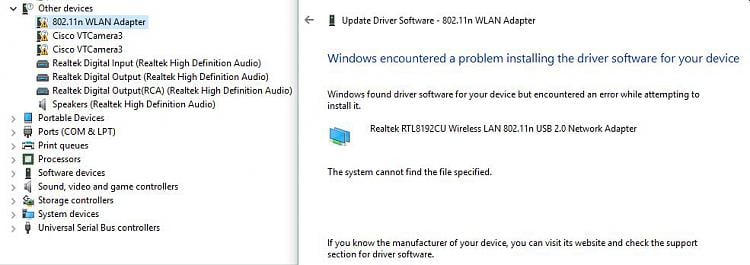
Fix 1: Deactivate Digital Driver Signature Authorization
It needs to be very well understood what’s in and what’s out of the VM for it to be used effectively. I was hit with Antivirus XP 2008 last month (AVG didn’t catch it) but, like Mary above, Malwarebytes cleaned it up. It’s a good download with rocketdrivers.com step-by-step instructions. If this doesn’t finish the problems I run HijackThis. If one is not experienced with this program I’d suggest that a trip to one of the many forums where they interpret HijackThis logs.
Module detected the file shortcut even if the file or folder was excluded. The Endpoint Security Service caused high CPU usage on Windows 10 and Windows Server 2012 systems. The Advanced Anti-Exploit module prevented Adobe Acrobat Reader to function in protected mode. The new monitoring mechanism displays on the endpoints the troubleshooting sessions in progress along with their statuses.